Secure Boot
On June 3, 2024, we are putting into production LAN-RING switches with FW 70, which has a rapidly increased level of security. The firmware includes many improvements, including a new bootloader with a set of Secure Boot tools. The primary purpose of the Secure Boot tool is to defend against unauthorized or malicious software, such as rootkits and other malware, that attempt to tamper with the boot process. It is achieved by verifying the digital signatures of crucial boot components before executing them.
Secure Boot support
| Series | Note |
| LAN-RING - F series | Supported in all switches produced from 1st June 2024 |
| LAN-RING - G series | Supported |
| IPLOG - G series | In 5/2024, only selected models | All models until the end of 2024 |
How works Secure Boot in LAN-RING switches from FW 70
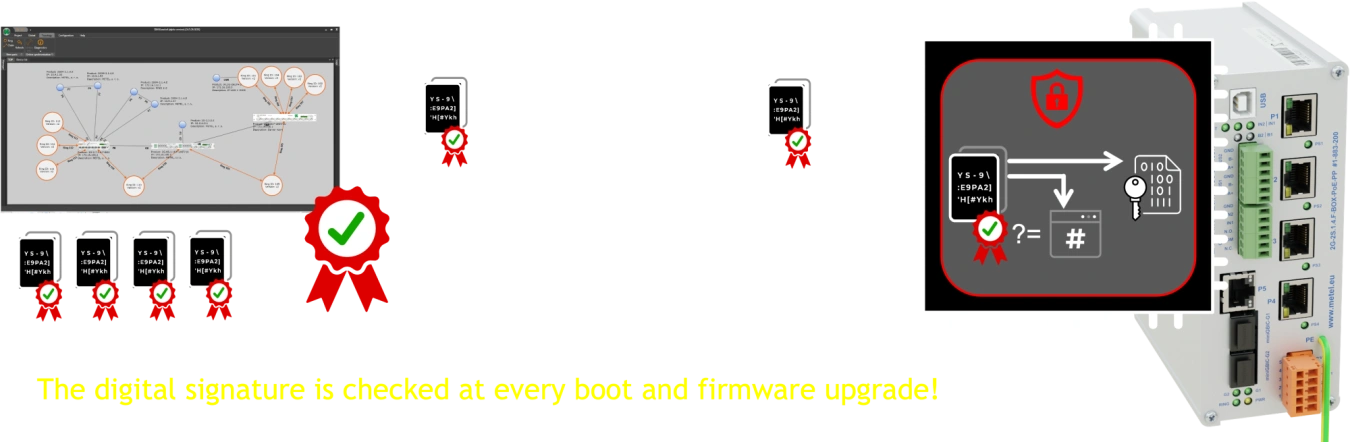
All new firmware images, starting with version 70, are digitally signed and encrypted.

The SIMULand application is also signed and contains the latest firmware.
The firmware image is transferred via an encrypted channel.
If the firmware image is received by the device, then it is fully validated. This validation consists of three steps:
Step 1. Verification before decryption.
Step 2. Decryption.
Step 3. Verification after decryption.
After validation, the image is stored in the internal FLASH memory.
Differences between bootloader versions
| RISKS | APPLIED MEASURES | |
| FW70 |
||
| BOOTLOADER 4 | BOOTLOADER 5 | |
| Outdated or fake version of the SIMULand | The application is digitally signed by a certificate that is part of the CA. The application automatically checks for the latest version. |
|
| Firmware modification in the PC | The firmware is encrypted and digitally signed, which is automatically checked before the FW upgrade. | |
| Risk "Man in the middle" | The transferred firmware is encrypted and digitally signed. Its authenticity is checked during the decryption process after transmission to the device. |
|
| External Flash memory replacement | The firmware is always checked before writening to internal flash. |
The firmware is always checked before writening to internal flash. Each time the device is turned on/restarted, the contents are checked to ensure that the part with the code used has not been changed. |
| Executable the fake code in the CPU | - | The firmware is booting only after checking the electronic signature RSA-4096. |
| Bootloader modification | A disassembled device's bootloader can only be deleted. It requires special tools. Deleting the bootloader causes the device to malfunction. |
The bootloader is digitally signed (SHA512). A disassembled device's bootloader can only be deleted. It requires special tools. Deleting the bootloader causes the device to malfunction. |

