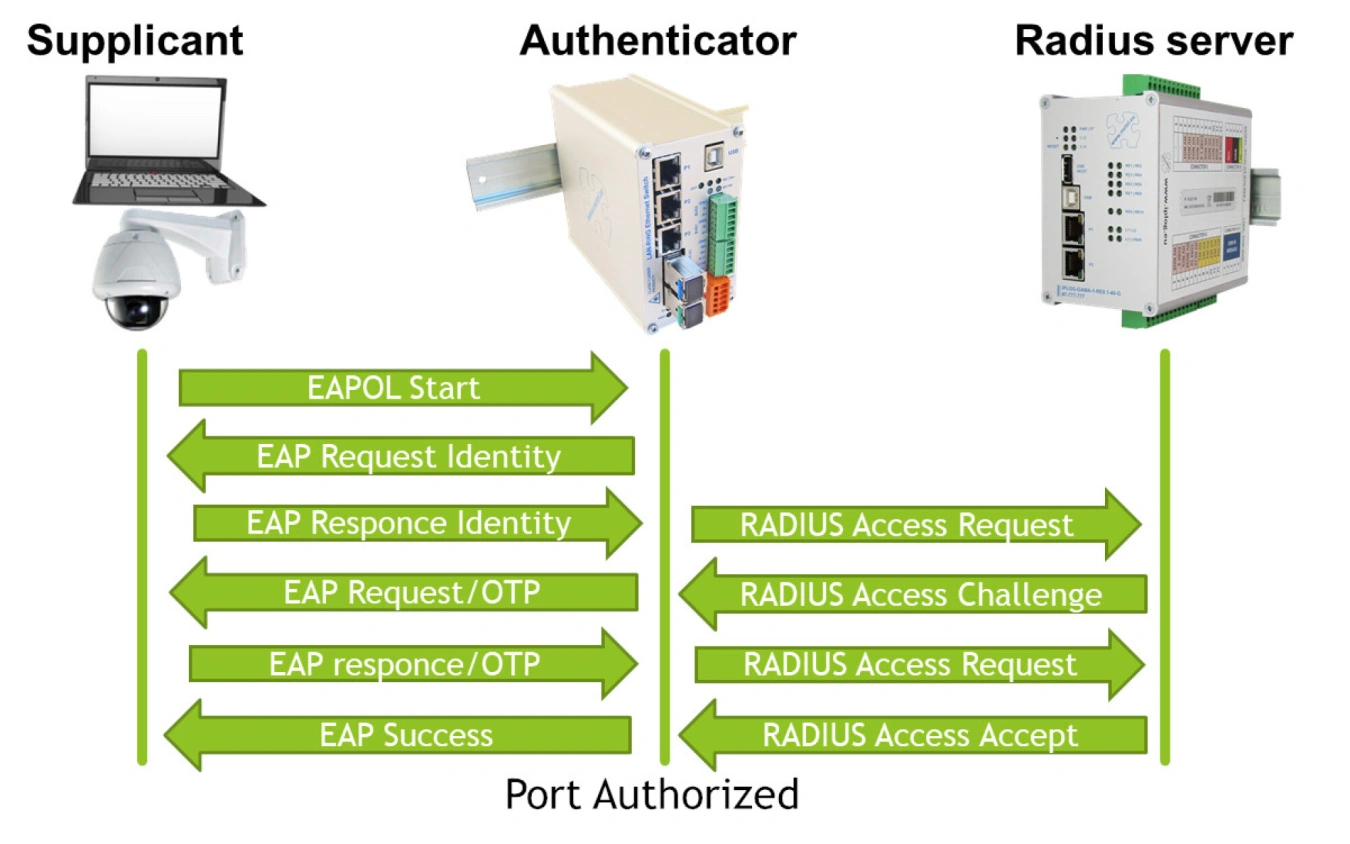
IEEE802.1X
The IEEE802.1X protocol is a very popular tool for user authentication. It has weaknesses in standard implementations. It can block unauthorized users from accessing the network, but that is all. In our implementation, we have added an important feature to help you increase security. All unauthorized users are immediately reported via SNMP TRAP to the visualization software. Therefore, a potential attacker could be caught immediately and would not have time to break into the network.
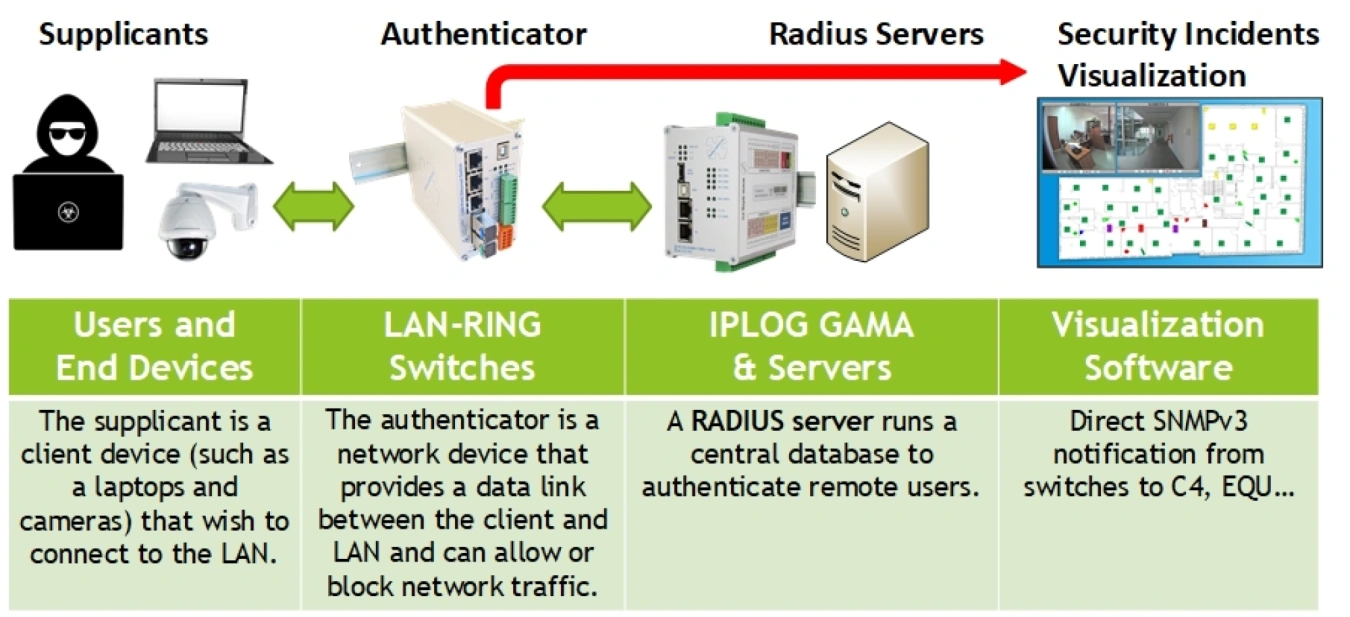
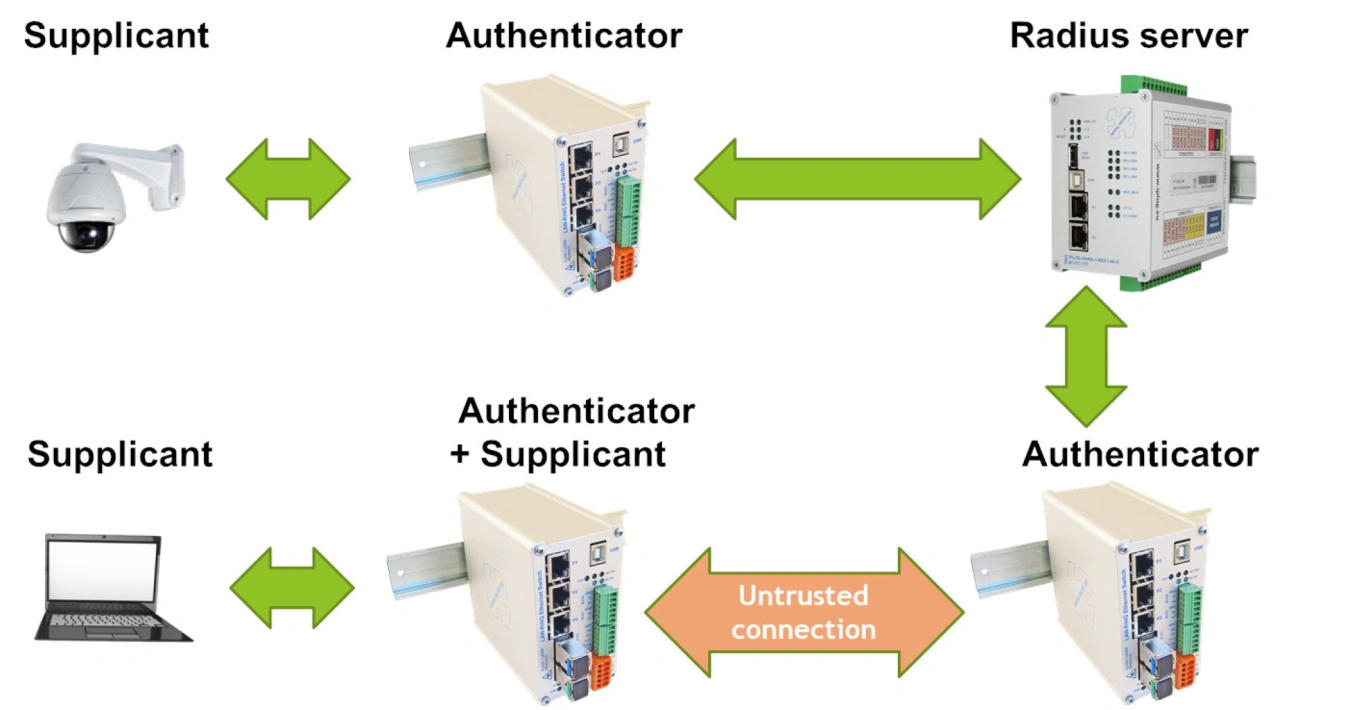
The IEEE 802.1X standard distinguishes 3 types of devices:
- Supplicant - an end user of the network who must be authenticated before accessing the network (technician with PC, camera).
- Authenticator - acts as an access point for the Supplicant. In LAN-RING networks, any managed switch with FW 62 or higher can have this role.
- Authentication server - usually a RADIUS server that decides to allow/deny network access requests. In systems with 802.1X user authentication, we recommend installing at least 2 redundant servers. At least one should be located directly on the protected object in a secure room (tamper, PZTS).
LAN-RING & IPLOG enables integrators to create a complete network infrastructure system with IEEE802.1X authentication independent of other vendors.
METEL authentication Radius server
We have developed the pkg package "free radius-server" for IPLOG-GAMA controllers. The control units' great advantage is their industrial operating temperature range from -40°C to +70°C. Unlike conventional servers, the IPLOG controllers can therefore be deployed in very harsh environments.
METEL authenticator/supplicant
LAN-RING F/G series switches support end-device authentication by the IEEE 802.1X standard.