Secure management via SNMPv3
A common feature of all our switches and PLCs is compatibility with SIMULand.v4, which communicates using the encrypted SNMPv3 protocol.
| Algorithm | Description | |
| Encryption | AES 256 | This is a symmetric key algorithm, which means the same key is used for both encryption and decryption. |
| Hash function | SHA 512 | A hash function is an algorithm used to create a unique, fixed-size digital fingerprint of data. The "SHA" stands for "Secure Hash Algorithm," and the "512" refers to the length of the hash value in bits. |
SIMULand's graphical interface makes configuration accessible to a wide range of users. According to the standards, communication is secured by the standardized AES encryption algorithm and protected by the SHA-1 hash algorithm against unauthorized modification of the transmitted data.
Compatibility with SIMULand App
| Series | Configuration via SIMULand | SSH CLIENT |
| LAN-RING - F series | Full support | - |
| LAN-RING - G series | Full support | Full support |
| IPLOG - G series | Basic network setting | Full support |
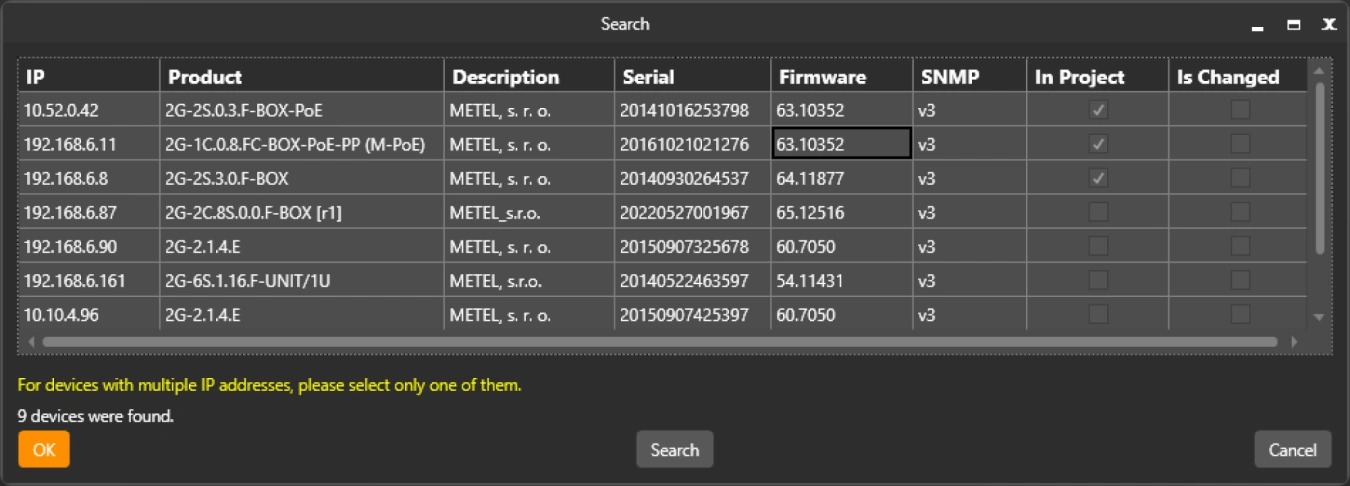
Discovery of all available devices on the LAN
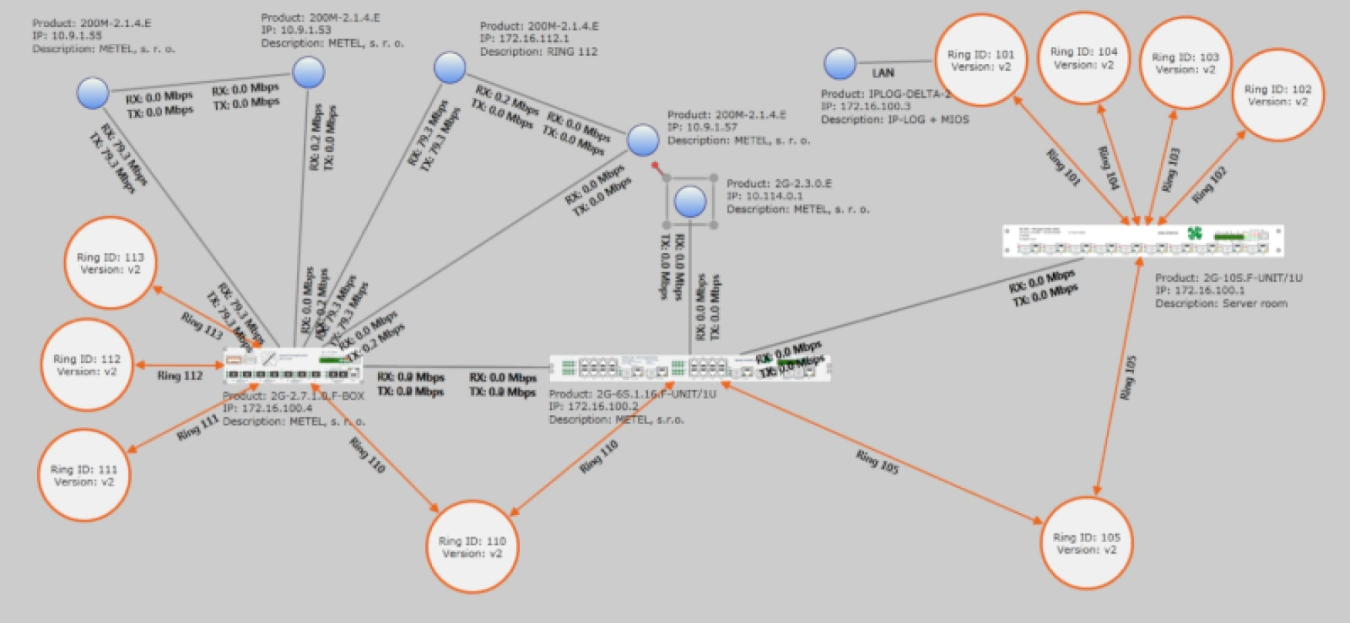
One of SIMULand's great strengths is the ability to automatically search for devices available on the LAN directly from the GUI.
Display of available devices in the topology
In addition, the SIMULandv4 application also includes a unique Topology tool that automatically displays all searched LAN-RING switches and IPLOG-GAMA controllers in the topology.