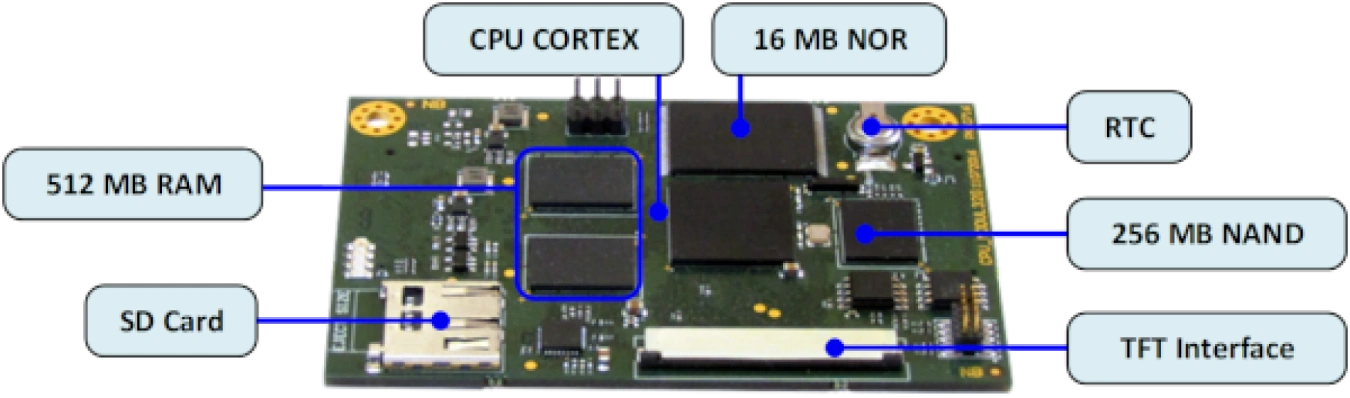
G series with SSH CLI
SSH allows the client and server to authenticate against each other using public and private keys, which prevents man-in-the-middle attacks. The protocol also has built-in mechanisms to protect against brute force attacks on login credentials. In addition, the protocol allows monitoring and auditing of access for security purposes. With these security features, the SSH CLI provides a secure way to remotely access and manage systems.